Location
National Cybersecurity Center of Excellence (NCCoE), 9700 Great Seneca Hwy, Rockville, MD 20850
Format
- Morning—Hybrid (in-person and virtual)
- Afternoon—In-person only
Background/Description
Recent advancements in Artificial Intelligence (AI) technology bring great opportunities as well as new or modified risks for organizations to manage, including impacts to their cybersecurity capabilities. These potential impacts of AI on cybersecurity need to be understood and managed. NIST is exploring how to best serve the cybersecurity community, building on and using its cybersecurity resources to assist organizations as they manage AI-related opportunities and risks. NIST’s early engagement with cybersecurity stakeholders has led to several initial observations:
- There is no consistent taxonomy or consensus on how AI advances inform organizations’ strategies for cybersecurity risk management.
- Cybersecurity leaders and professionals must strategically address emerging cybersecurity risks stemming from advancements in AI, even as they continue to manage ongoing operations.
- These professionals would benefit from informed guidance and additional resources to help them shape their strategies as well as organize and prioritize their actions.
- AI introduces new and modified challenges with potentially major impacts regarding cybersecurity – but AI advances do not necessarily require fundamental changes to the way organizations address cybersecurity. Existing cybersecurity standards, frameworks, guides, and practices can still be effective when used individually and together if they are applied or modified to specifically address AI-related challenges as well as AI’s helpful capabilities.
To address these cybersecurity concerns, NIST is proposing the creation of a NIST Cybersecurity Framework (CSF) Profile, partnering with the cybersecurity and AI communities. This workshop will explore the ideas discussed in the Cybersecurity and AI Workshop Concept Paper (please provide any feedback using the form found on our project page before 11:59 p.m. EDT on Friday, March 14, 2025, to inform workshop topics).
Construction at NCCoE
Please note there is ongoing construction in areas surrounding NCCoE. Please proceed with caution and follow all construction personnel and signage instructions while onsite.
CE/CPE Credits
NIST does not provide specific information regarding CE credits. Attendees are welcome to use their registration confirmation as a means to self-report to their authoritative certification bodies.
Recording Note: Portions of the event may be recorded and audience Q&A or comments may be captured. The recorded event may be edited and rebroadcast or otherwise made publicly available by NIST. By registering for — or attending — this event, you acknowledge and consent to being recorded.
,
Agenda
| Time | Topic | Location | Speaker |
|---|---|---|---|
| 08:30—9:00 | Arrival and Check-in | Room 3ABC + Livestream | N/A |
| 9:00—9:10 | Welcome and Opening Remarks | Room 3ABC + Livestream | James St. Pierre, NIST |
| 9:10—9:20 | NCCoE Welcome | Room 3ABC + Livestream | Cherilyn Pascoe, NIST |
| 9:20—9:50 | Setting the Stage for the Cyber AI Profile | Room 3ABC + Livestream | Katerina Megas, NIST |
| 9:50—10:10 | Fireside Chat: Potential Interplays Between the CSF and AI RMF for cybersecurity | Room 3ABC + Livestream | Moderator: Dan Caprio, DLA Piper Panelists:
|
| 10:10—10:20 | Break | ||
| 10:20—11:05 | Panel: Protection of AI Systems | Room 3ABC + Livestream | Moderator: Vicky Pillitteri, NIST Panelists:
|
| 11:05—11:50 | Panel: Defensive and Adversary Use of AI | Room 3ABC + Livestream | Moderator: Martin Stanley, NIST Panelists:
|
| 11:50—12:00 | Morning Wrap-up and Afternoon Breakout Session Plans | Room 3ABC + Livestream | Katerina Megas, NIST |
| 12:00—1:30 | Lunch Break (on your own) |
Afternoon Sessions (in-person only)
Overview of Breakout Session Tracks
(see map below for room locations)
The breakout sessions provide an opportunity for participants to share insights and feedback to inform the Cyber AI Profile. Participants will rotate to complete each of the three sessions.
- Track A - Focus Area Descriptions: The concept paper proposed three focus areas for the Cyber AI Profile: Securing AI System Components, Thwarting AI-enabled Cyber Attacks, and Using AI for Cyber-defense Activities. The purpose of this track is to review the language used to describe each focus area presented in the concept paper, identify any new focus areas that should be considered within the scope of the Cyber AI Profile, and identify the key characteristics of each focus area.
- Track B – Anticipated Profile Uses and Elements: The Cyber AI Profile will be a tool for helping organizations understand and manage risk at the intersection of AI and cybersecurity. The discussions during this track will focus on anticipated uses of the Profile and information the Profile should include to help organizations use it. Discussions will explore whether and how to include: specific implications of cybersecurity for AI and AI for cybersecurity, CSF Subcategory priorities, mappings, and informative references. This track will also include discussions regarding how to reflect the roles of complementary frameworks.
- Track C - Priorities in the CSF Core: The Cyber AI Profile will use the outcomes in the CSF 2.0 Core to organize discussions regarding risk. The purpose of this track is to review areas of emphasis that are emerging from early research, discuss threats and mitigations that will further inform areas of emphasis, and discuss additional resources that can inform how the CSF Core is applied in the Cyber AI Profile.
| Time | Topic | Location | Speaker |
|---|---|---|---|
| 1:30—2:25 | Breakout Sessions—Round #1 Tracks:
| A: Room 5 B: Room 3ABC C: Room 3D | Breakout Facilitators:
|
| 2:25—2:35 | Transition/Break | ||
| 2:35—3:30 | Breakout Sessions—Round #2 Tracks:
| A: Room 5 B: Room 3ABC C: Room 3D | Breakout Facilitators:
|
| 3:30—3:40 | Transition/Break | ||
| 3:40—4:35 | Breakout Sessions—Round #3 Tracks:
| A: Room 5 B: Room 3ABC C: Room 3D | Breakout Facilitators:
|
| 4:35—4:40 | Transition/Break | ||
| 4:40—5:00 | Workshop Close-out and Next Steps | Room 3ABC |
|
Map of Breakout Session Track Locations
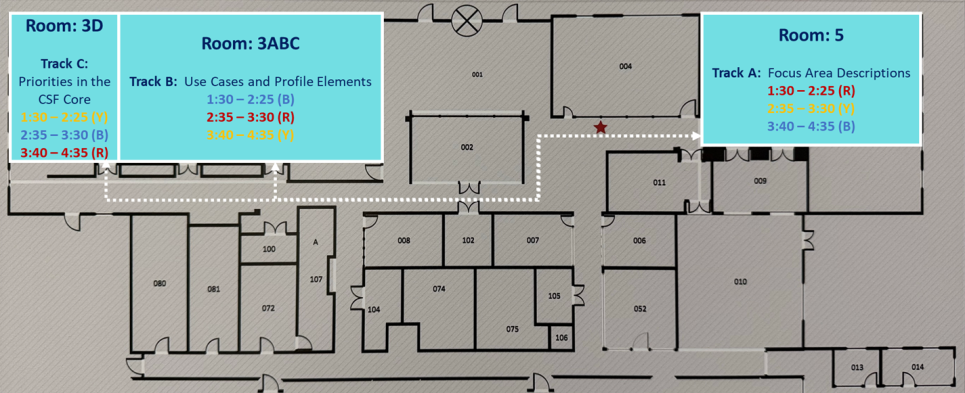
Please visit each track at the color-coded times below that correspond to the sticker on your badge to help us ensure there is room for everyone in each session.
Presentation Slides
Workshop Recording
The recording for this workshop is now available.

